What is Encryption?
Encryption is a method of preventing unauthorized access to electronic data. It is used to protect data on devices such as computers, laptops, cellphones, or USB sticks. It can also be used to protect data during transmission. For example, after you enter your credit card details to purchase something online, your computer automatically encrypts that data so that others cannot steal this information when it is transmitted over the internet.
Encryption is imperative for sending sensitive information, securing your documents, keeping your email private and, ultimately, it allows for peace of mind if a computer is misplaced, lost or stolen.

What Happens When I Encrypt My Devices?
Encryption is the process of scrambling information, making it unreadable to protect it from unauthorized access. When data is encrypted, you need a password to make it readable again.
Encrypting your computer and mobile devices is the most effective way to secure your personal information and UBC’s data.
Why Should I Encrypt My Devices?
At UBC, we are regulated by the Freedom of Information and Protection of Privacy Act (FIPPA), which requires us to protect personal information from unauthorized collection, use, or disclosure.

In support of the law, UBC policy requires that all Devices—whether UBC-owned or personally-owned—used to access UBC Electronic Information and Systems be encrypted. Learn more in UBC’s Information Security Standard U5, Encryption Requirements.
Security breaches can cause a lot of wasted time, money, and stress, and can harm the university's reputation. But, if your device is misplaced, lost or stolen, encrypted data will be unreadable without a password.
Devices are replaceable; personal or private information is not.
Concerned about travelling with an encrypted mobile device? Learn about travelling with electronics.
How Do I Request Encryption?
If you are using a UBC-owned Device, encryption is provided for UBC faculty and staff at no cost.
You can request encryption by contacting your faculty or department’s local IT support.
An overview of the encryption process for common devices and operating systems is outlined below:
Windows
Encryption Overview – what you need to know for Windows computers
Reminder: even an encrypted device is vulnerable if it does not have proper password protection. Your password should be unique, comply with the UBC password policy, and if used as an encryption password comply with the key escrow requirements.
- To check your computer to see if it has been encrypted, follow the instructions here.
- The software takes less than 10 minutes to install per computer.
- This software has little to no noticeable performance impact on your computer once the full encryption process is complete. Typically this takes 1-3 days.
- You can also use your computer as usual immediately after the installation.
- Restarting, sleeping, hibernating, and shutting down the computer will have no impact on the encryption process.
- You will be prompted to restart a few times. Please follow the instructions on the screen. Do not be alarmed by restarts.
- Encryption typically takes 1-3 days to apply. Occasionally it can take up to 2 weeks. You do not need to check on the progress. Please be patient.
How to confirm which version of Windows operating system you are running
To find out which version of Windows your device is running, press the Windows logo key + R, type winver in the Open box, and then select OK. Here’s how to learn more:
- Select the Start button > Settings > System > About.
- Under Device specifications > System type, see if you're running a 32-bit or 64-bit version of Windows.
- Under Windows specifications, check which edition and version of Windows your device is running.
Windows 8 (core)
Contact your local IT Support to check if upgrading your Operating System is possible.
Windows 8 (RT)
- This operating system version is primarily for Tablet systems.
- Microsoft’s Bitlocker native encryption solution is not supported on this operating system.
- It is vitally important that you follow UBC’s safe data storage and data classification policies [PDF]
Windows 8 Professional or Enterprise
- Microsoft’s Bitlocker native encryption solution will work on this version of Windows.
Window 10 Home
Contact your local IT Support to check if upgrading your Operating System is possible.
Windows 10 Professional, Enterprise or Education
- Microsoft’s Bitlocker native encryption solution will work on this version of Windows.
Windows systems with RAID
- You should contact your local IT Support and discuss safely storing data which includes personal information
- We have no supported way of encrypting most systems which use software RAID configurations
- It is vitally important that you follow UBC’s safe data storage and data classification policies [PDF]
Mac
Encryption Overview - what you need to know for Mac computers
Reminder: even an encrypted device is vulnerable if it does not have proper password protection. Your password should be unique, comply with the UBC password policy and if used as an encryption password comply with the key escrow requirements.
- To check your computer to see if it has been encrypted, follow the instructions here.
- The software takes less than 10 minutes to install per computer.
- This software has little to no noticeable performance impact on your computer once the full encryption process is complete. Typically this takes 1-3 days.
- You can also use your computer as usual immediately after the installation.
- Restarting, sleeping, hibernating, and shutting down the computer will have no impact on the encryption process.
- Once the software is installed, everything happens in the background, invisible to you. You will be prompted to restart a few times. Please follow the instructions on the screen. Do not be alarmed by restarts.
- Encryption typically takes 1-3 days to apply. Occasionally it can take up to 2 weeks. You do not need to check on the progress. Please be patient.
OS X 10.8.2 and above
- We use a solution called McAfee Management of Native Encryption (MNE)
- McAfee MNE partners with the Apple native encryption which is called Filevault v2.0
- The log in process remains the same, you log in to your computer using your usual login username and password.
OS X 10.7 and below
- The encryption service does not support your Operating System.
- Contact your local IT Support to check if upgrading your Operating System is possible.
OS X systems with RAID
- You should contact your local IT Support and discuss safely storing data which includes personal information
- We have no way of encrypting most systems which are RAID configured
- It is vitally important that you follow UBC’s safe data storage and data classification policies [PDF]
Linux
Encryption Overview – what you need to know for Linux computers
Reminder: even an encrypted device is vulnerable if it does not have proper password protection. Your password should be unique, comply with the UBC password policy, and if used as an encryption password comply with the key escrow requirements.
We will soon be recommending encryption standards for Linux devices. In the meantime:
- It is vitally important that you follow UBC’s safe data storage and data classification policies [PDF]
- You should contact your local IT Support and discuss safely storing data which includes personal information
Mobile Devices
For information about encrypting mobile devices, including smartphones, tablets and mobile storage devices, please see the What are the options for encrypting my own device? section below.
What Are The Options for Encrypting My Own Device?
If you are using your own personal (non-UBC-supported) device to access UBC Electronic Information and Systems, then it is your responsibility to ensure that it is encrypted. To check your computer to see if it has been encrypted, follow the instructions on the UBC IT Knowledge Base.
Windows
If you have a Microsoft-based system and you are running one of the following operating systems, then you can use Microsoft's BitLocker encryption tool:
- Windows 8/8.1: Pro and Enterprise Editions
- Windows 10: Pro, Education, and Enterprise Editions
How to encrypt a Windows computer with BitLocker
If you are running Windows 10 Home, you may be able to use Microsoft device encryption. Not all devices that run Windows 10 Home can use Microsoft device encryption. To see if your device meets the requirements, please see the Device encryption in Windows 10 article on the Microsoft website.
UBC students: Currently enrolled UBC students with a valid CWL account qualify for one license of Windows 10 Education. Visit the UBC IT website for more information. In addition, you may be able to sign up for a Windows 10 Education licence at the Microsoft Azure Dev Tools for Teaching Website (as well as getting access to some other great tools).
How do I know which Windows Operating System I have?
To find out which version of Windows your PC is running, press Windows logo key + R on your keyboard, type winver then press Enter.
What if I don't have one of these versions of Windows?
We recommend that you upgrade to a version of Windows that will support BitLocker. If this isn't an option, and the version of Windows on your personally owned computer does not support native BitLocker encryption (e.g. Windows 10 Home), then the best route to encrypt your computer is to use VeraCrypt. VeraCrypt is a technical tool and it is very important to follow all of the following steps carefully:
Mac
If you have an Apple machine running macOS then you can use Apple's FileVault encryption.
Linux
If you are using your own personal (non-UBC-supported) device to access UBC Electronic Information and Systems, then it is your responsibility to ensure that it is encrypted.
Both VeraCrypt and dm-crypt/LUKS are common encryption options, allowing a user to encrypt either a full disk during installation or a new volume.
Full Disk Encryption
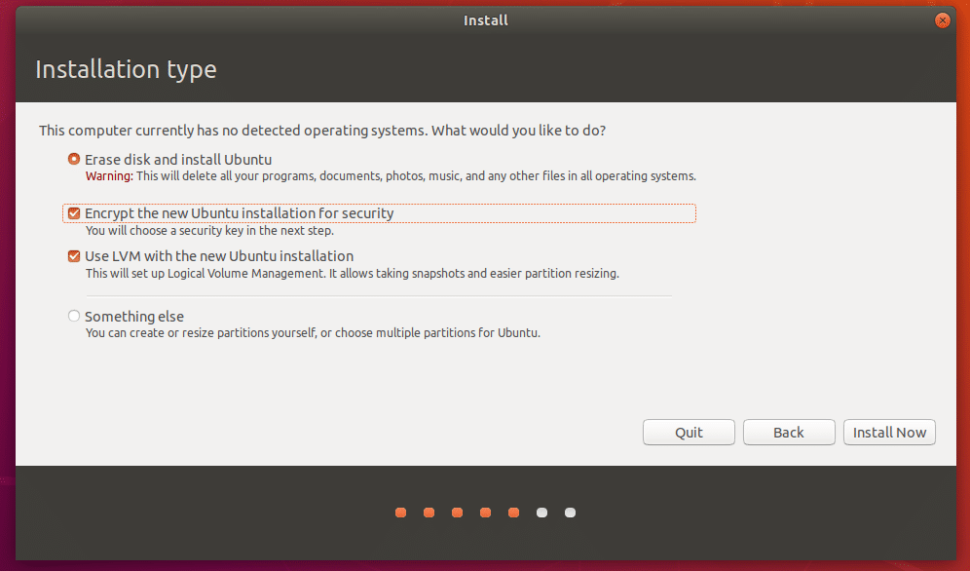
All modern desktop Linux instances have a full disk encryption option at installation that simply involves checking a box and setting a security key. See the example for Ubuntu in Figure 1 below.
You must remember your password which unwraps the security key. It is isolated on your device, and UBC IT will not have access. You will be required to enter this password at every boot, and you will no longer be able to remotely reboot your system.
It is recommended that you save a copy of your security key (not password) to your personal network storage drive (UBC Home Drive - Vancouver; F: Drive - Okanagan), so that University IT Support Staff can assist you in the event of an incident.
This is very important. If you do not know your password and you lose access to your security key, there is no way to access your data. See the options available to users to store their encryption recovery keys (security key) in the Encryption FAQ.
There is no easy way to encrypt a system that is already built. To set-up full disk encryption on devices that already have Linux installed, the only way is to backup all your data, reinstall Linux (with encryption enabled), reinstall all your applications and then restore your data.
Due to operability or performance constraints, this is not always viable. Please see the guidance from Information Security Standard U5, Encryption Requirements
Encrypting a partition or new volume
Native tools are available in common Linux desktops are available to encrypt a new volume or partition.
Online Guides
- Cryptsetup and LUKS - open-source disk encryption
- VeraCrypt (downloadable software packages and installation instructions)
- Securing Red Hat Enterprise Linux 8 (PDF, see Chapter on Encrypting Block Devices using LUKS)
- How to Encrypt a Drive on Ubuntu 18.04
Getting Help
If you have any questions or concerns, please contact privacy.matters@ubc.ca.
Smartphones & Tablets
Reminder: Even an encrypted device is vulnerable if it does not have proper password protection. Your password should be unique, comply with the UBC password policy, and if used as an encryption password comply with the key escrow requirements.
iPhone and iPads
How do I know if my device is encrypted?
iPhones and iPads are not encrypted by default. However, if you password protect the device or use a thumb/fingerprint to access the device, it is encrypted.
How do I encrypt?
Turn on a passcode (which can be found under setting, usually in the “Touch ID & Passcode” submenu.)
All other phones and tablets
How do I know if my device is encrypted?
Android, Windows and BlackBerry phones and tablets are not encrypted by default, so if you are not sure, your device is probably not encrypted.
Having to enter a password to access the device does not guarantee it is encrypted.
Different versions of Android, Windows and Blackberry devices place their encryption settings behind different menus.
You can often see if your device is encrypted under menus such as “System”, “Security” and “Passcode”, and “Encryption”. You can often find device specific instructions by doing an internet search for your device and the word encryption.
If in doubt, contact your departmental IT support.
How do I encrypt?
In most cases, if you were able to find the menu that told you that your device is encrypted the option to encrypt is in the same location.
Check with your local IT Support or device provider if you have questions about encrypting.
For BlackBerry 10: Go to Settings > Encryption. Set Device Encryption to ON & set the device password
Mobile Storage Devices (e.g. memory and hard drives)
How do I know if my device is encrypted?
When storage devices are encrypted, the encryption software used will normally ask for a password when you plug it into your USB port.
You can encrypt specific files and folders on USB sticks using freely available encryption tools such as 7zip. UBC has also provided instructions on how to encrypt an external USB drive using BitLocker (Windows), VeraCrypt (Windows) and FileVault (Mac).

Frequently Asked Questions
Do I need to encrypt my desktop computer?
Yes. As per Information Security Standard U5, Encryption Requirements, encryption requirements apply to all Devices, whether UBC-owned or personally-owned, that are used to access UBC Electronic Information and Systems.
If I use my personally-owned computer to access my on-campus (work) computer via RDP, am I required to encrypt my personally-owned computer?
As per Information Security Standard U5, Encryption Requirements, encryption requirements apply to all Devices, whether UBC-owned or personally-owned, that are used to access UBC Electronic Information and Systems.
However, if a personally-owned desktop or laptop computer is ONLY accessing UBC Electronic Information and Systems through Remote Desktop Protocol (RDP) or UBC's Virtual Desktop Interface (VDI) sessions then encryption is not required at this time, but is recommended.
- Connecting via VPN - encryption is required
- Connecting via VPN + RDP - encryption is recommended but not required at this time
- Connecting via VDI - encryption is recommended but not required at this time
What encryption options are available for Windows 10 Home edition? How can I encrypt without upgrading my operating system? Are there other options?
UBC has put together a guide for how to encrypt a Windows computer with VeraCrypt.
Are there any exemptions to the encryption requirements for machines that are not internet-facing?
Includes private or non-routed networks in labs.
According to Information Security Standard U5, Encryption Requirements, there is no exemption to the requirements. However, local IT Support Staff should focus on the highest risk and highest volume devices first, before tackling more complex use cases. The Cybersecurity team is available to help with more complex use cases.
Is there an intention to update the current Information Security Standards to reflect the change to encryption for desktop computers?
The Information Security Standards are living documents and are constantly under revision to keep up with the ever-changing nature of Information Security and the internal changes at UBC. We will make updates to the Information Security Standards to reflect any ongoing requirements as and when we can.
Is encryption risky? What happens if I lose my encryption recovery key?
Encryption is not risky if you take the following steps:
- Before you encrypt your computer, back up your computer on an external hard drive.
- Follow the instructions to encrypt your device on this page.
- Save your encryption recovery key in a safe place off of the computer (see guidance in the question below).
In the event that you lose your encryption recovery key, there is nothing that UBC can do to recover your data.
It is critical that you store your key in one, or preferably more than one, of the places outlined in the guidance for the question below.
What options are available to users to store their encryption recovery keys?
Windows: It is highly recommended that you allow Microsoft store your recovery key using your Microsoft Account. You should also store your encryption recovery key using another one of the methods outlined under All Operating Systems below.
Mac: It is highly recommended that you allow iCloud store your recovery key using your Apple ID account (Apple account). You should also store your encryption recovery key using another one of the methods outlined under All Operating Systems below.
All Operating Systems: Whether or not you store your encryption recovery key with Apple or Microsoft, we recommend that you also generate a recovery key when you enable encryption and save it to a safe place off of the PC which you are encrypting. Some options for storing your encryption recovery key include:
- Saving your recovery key to your personal network storage drive – We recommend that you save your recovery key to your personal network storage drive (UBC Home Drive - Vancouver; F: Drive - Okanagan) so that University IT Support Staff can access this in the event that your require it.
- Saving your recovery key to your password manager – You can use a password manager to store your recovery key. Some examples of popular password managers include Bitwarden, LastPass and KeePass. Do not save your recovery key in your internet browser passwords. Learn more about Password Managers.
- Saving your recovery key to a secure Cloud Storage Service – Store a copy of your recovery key in a safe place off of the PC, like a secure Cloud Storage Service which is only accessible to you. Some examples of Cloud Storage Services include iCloud, Dropbox, Google Drive, OneDrive and Box.
- Saving your recovery key to a secure hard drive – Store a copy of your recovery key in a safe place off of the PC, like a secure hard drive which is only accessible to you. Storing recovery keys on a hard drive may be higher risk as a hard drive could be prone to failure.
- Printing your encryption recovery key and locking it away - Print your encryption recovery key and put it in a safe or lockable cabinet which is always kept locked and secure.