Know the warning signs
What is Phishing and Spear Phishing?
A phishing attack is when a criminal attempts to trick unsuspecting users into giving them their login information through an electronic communication. Most common to UBC are email messages sent with a deceptive link in the message that may appear to have one destination, but actually leads to another. Links may be disguised with lookalike domain names that are one letter off from legitimate ones when in actuality they redirect to a webpage that is a repository for the criminal to capture the victim’s login credentials.
Spear Phishing campaigns, on the other hand, appear to come from a trusted source that is closer to the target. Cybercriminals send these personalized emails to one person or a few persons who share a connection, such as working in the same department.

What is 'Self-Phishing'?
One way that a criminal may attempt to obtain protected information that is critical to the security of the University is through a phishing attack. Whether or not the criminal is successful is often contingent upon establishing trust with their victim. In some cases it could simply be the criminal trying their luck!
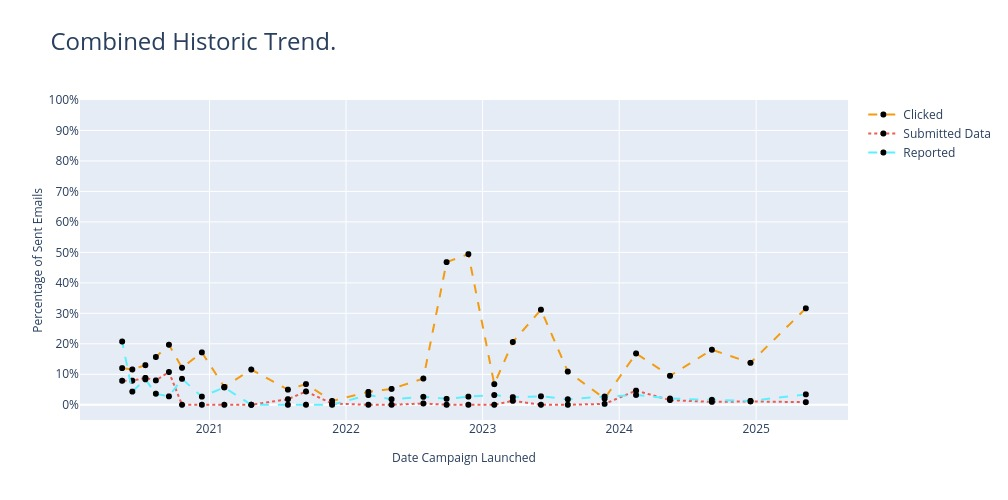
The hard truth is that UBC is constantly being phished! Believe it or not, criminals typically use a customer relationship management tool to track the response rates and engagement statistics of their phishing campaigns so they can further target individuals who have already responded to a phish.
To help employees better understand how they can quickly spot some of the most common types of phishing and avoid falling victim to their attacks, the UBC Cybersecurity team has established a Self-Phishing training exercise. This means that, after first warning units that an ‘attack’ is imminent, we send our own phishing messages (crafted to look just like the criminals) to UBC employees!
The objective is to increase the reporting of phishing messages to security@ubc.ca and reduce success rates from the criminal’s perspective. Ideally, if we can make UBC "unresponsive" to criminals, then they will likely ‘move on’ to an easier and more responsive target.
Latest campaign
Data current as of: May 22, 2025